Backstory of the PC build
My wife and I had ordered some new lamps for our bedroom, when we got a package that had everything BUT our new lamps! After opening the box, I found there was a VERY nice graphics card inside, especially during the graphics card price hike we’ve been seeing going on.
Needless to say, after contacting the company about the mistake, we were apologized to, and told to keep the contents of the package we had received..
After months of this graphics card, an AMD Radeon RX 6900XT had been sitting in my office, and a few awesome birthday gifts. I ended up finally getting to start a new PC build!
Build List:
- AMD Ryzen 5900x
- RX 6900 XT
- 64 GB DDR4 3200 mhz
- 850GT EVGA Power Supply
- Strix B550-F Gaming Mobo
- 2TB NVME SSD 970 Evo
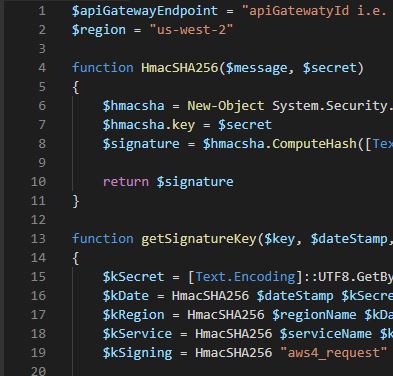
Powershell script that enables you to call out to AWS API Gateway on a given node.
$apiGatewayEndpoint = "apiGatewatyId i.e. m123abc2d1"
$region = "us-west-2"
function HmacSHA256($message, $secret)
{
$hmacsha = New-Object System.Security.Cryptography.HMACSHA256
$hmacsha.key = $secret
$signature = $hmacsha.ComputeHash([Text.Encoding]::ASCII.GetBytes($message))
return $signature
}
function getSignatureKey($key, $dateStamp, $regionName, $serviceName)
{
$kSecret = [Text.Encoding]::UTF8.GetBytes(("AWS4" + $key).toCharArray())
$kDate = HmacSHA256 $dateStamp $kSecret;
$kRegion = HmacSHA256 $regionName $kDate;
$kService = HmacSHA256 $serviceName $kRegion;
$kSigning = HmacSHA256 "aws4_request" $kService;
return $kSigning
}
function hash($request)
{
$hasher = [System.Security.Cryptography.SHA256]::Create()
$content = [Text.Encoding]::UTF8.GetBytes($request)
$bytes = $hasher.ComputeHash($content)
return ($bytes|ForEach-Object ToString x2) -join ''
}
function GETAPIGatewayResponse($nodeIp, $request) {
$br = [regex]::Unescape('\u000a')
#$access_key = aws configure get aws_access_key_id --profile $credName
#$secret_key = aws configure get aws_secret_access_key --profile $credName
$now = [DateTime]::UtcNow
$amz_date = $now.ToString('yyyyMMddTHHmmssZ')
$datestamp = $now.ToString('yyyyMMdd')
$service = "execute-api"
$method = "GET"
$apiGatewayId = $apiGatewayEndpoint
$host1 = "$($apiGatewayId).execute-api.$($region).amazonaws.com"
$signed_headers = 'host'
$credential_scope = $datestamp + '/' + $region + '/' + $service + '/' + 'aws4_request'
$canonical_querystring = ''
$canonical_querystring = 'X-Amz-Algorithm=AWS4-HMAC-SHA256'
$canonical_querystring += '&X-Amz-Credential=' + [uri]::EscapeDataString(($access_key + '/' + $credential_scope))
$canonical_querystring += '&X-Amz-Date=' + $amz_date
$canonical_querystring += '&X-Amz-SignedHeaders=' + $signed_headers
$canonical_headers = 'host:' + $host1 + $br
$canonical_request = $method + $br
$canonical_request += "/test/host/" + $nodeIp + "/" + $request + $br
$canonical_request += $canonical_querystring + $br
$canonical_request += $canonical_headers + $br
$canonical_request += $signed_headers + $br
$canonical_request += hash -request ""
$algorithm = 'AWS4-HMAC-SHA256'
$canonical_request_hash = hash -request $canonical_request
$string_to_sign = $algorithm + $br
$string_to_sign += $amz_date + $br
$string_to_sign += $credential_scope + $br
$string_to_sign += $canonical_request_hash
$signing_key = getSignatureKey $secret_key $datestamp $region $service
$signature = HmacSHA256 -secret $signing_key -message $string_to_sign
$signature = ($signature|ForEach-Object ToString x2) -join ''
$canonical_querystring += '&X-Amz-Signature=' + $signature
$request_url = "https://" + $host1 + "/test/host/" + $nodeIp + "/" + $request + "?" + $canonical_querystring
Write-Host "Request: $($request), RequestUrl: $($request_url)"
$StandardHeaders = @{
"Accept"="application/json"
"Content-Type"="application/json"
}
$apiGatwayResponse = Invoke-WebRequest -Method GET -Headers $StandardHeaders -Uri $request_url
if([int]$apiGatwayResponse.StatusCode -ge 200 -AND [int]$apiGatwayResponse.StatusCode -lt 300) {
#do something with response
} else {
Write-Host "Request to $($request_url) failed"
}
}
GETAPIGatewayResponse -nodeIp "127.0.0.1" -request "api/endpoint"

Hello to anyone and thank you for visiting to whomever may be reading this!









